Windows Forensics Workshop
CASE OVERVIEW: You have been given a system that has been used for some illegal activity were the user accessed confidential files that the user was not supposed to access. The system has two user accounts which are the main suspects involved in this case (« joker » and « IEUser »). You are required to provide answers to all the questions below by providing evidence (proof) with details and screenshots. Remember: SCREENSHOT OR IT DID NOT HAPPEN 😉
Link : (https://archive.org/details/BSidesAmman21.E01)
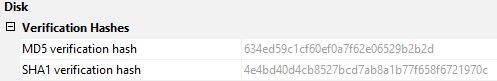
Question 1: What is the hash value for the given forensic image?
Question 2: Which user account was used to access some confidential documents?
Joker
Question 3: Explain in detail what proof do you have to support your answer?
Users\Joker\AppData\Local\Microsoft\Windows\WebCache\V0100001.log : file://192.168.70.128/SharedJJ/docs/Confidential.rtf : 15/02/19 05:03:25UTC
Question 4: Did the user access the confidential files from a local drive or network location?
Network location
Question 5: What proof do you have to support your answer?
192.168.70.128/SharedJJ/docs/ = Network Location
Question 6: List all the files that were accessed with full paths.
C:\Users\Joker\Confidential.rtf
file://192.168.70.128/SharedJJ/docs/Confidential.rtf
file://192.168.70.128/SharedJJ/docs/Confidential_02.docx
file://192.168.70.128/SharedJJ/docs/Confidential_03.docx
file://192.168.70.128/SharedJJ/docs/Confidential_04.docx
Question 7: Provide two different evidence to prove that those files were truly accessed.
1/Users\Joker\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\469e4a7982cea4d4.automaticDestinations-ms :
- \192.168.70.128\SharedJJ\docs\Confidential_04.docx
- \192.168.70.128\SharedJJ\docs\Confidential_03.docx
- \192.168.70.128\SharedJJ\docs\Confidential_02.docx
- \192.168.70.128\SharedJJ\docs\Confidential.rtf
- \Users\Joker\Confidential.rtf
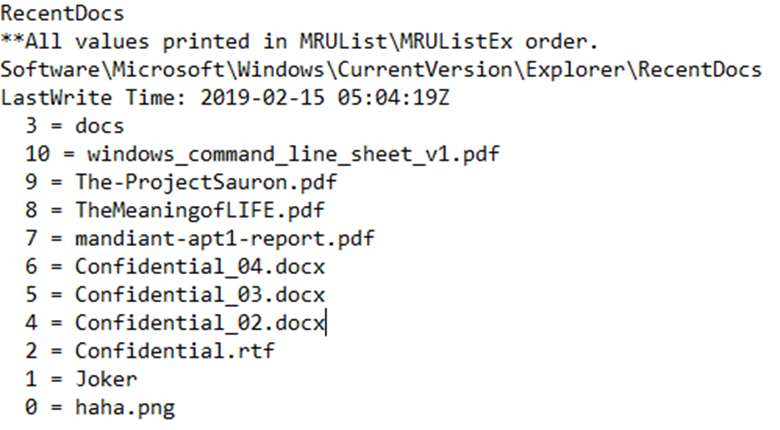
2/Most Recents Used from Joker’s Ntuser.dat :
Question 8: Which application was used to open any of the confidential document(s)?
According to the Windows TimeLine, (Users\Joker\AppData\Local\ConnectedDevicesPlatform\L.Joker\ActivitiesCache.db table activity columns payload and AppId) wordpad.exe has been used :

« {6D809377-6AF0-444B-8957-A3773F02200E}\\Windows NT\\Accessories\\wordpad.exe »,
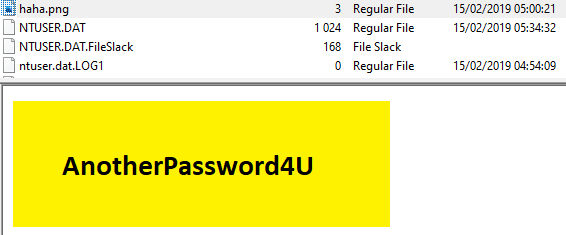
The next three questions are related to the image with the text « AnotherPassword4U » found inside the user’s home directory.
Question 9: What is the full path to the files of interest?
Users\Joker\haha.png
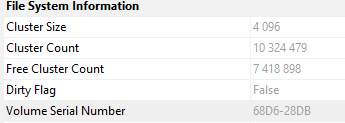
Question 10: What is the Volume Serial Number where the file exists?
Question 11: What are the Modified, Accessed, and Creation (MAC) timestamps in UTC for the file?
Modified 15/02/19 05:00:21
Acceded 15/02/19 05:00:22
Created 15/02/19 05:00:21
The DCode.exe application was used by one of the users. Provide evidence to the next four questions below, but, be careful, this is a tricky question!!!
Question 12: Which user do you think ran the application and what evidence do you have to support your hypothesis?
dd.exe & DCode.exe are the sames files, SHA1 : 46f0f39db5c9cdc5fe123807bb356c87eb08c48e.

SYSTEM\ControlSet001\Control\Session Manager\AppCompatCache : C:\Users\Joker\dd.exe
Joker is the user.
Question 13: How many times was it used?
According to UserAssist key (NtUser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}, and (Users\Joker\AppData\Local\ConnectedDevicesPlatform\L.Joker\ActivitiesCache.db), just one time. ,
Question 14: When was it last used?
15/02/19 05:02:12UTC
Question 15: Where was the application located (full path)?
C:\Users\Joker\dd.exe
