Like Qualcomm chipsets, Kirin chipsets that equip many Huawei/Honor devices have a secondary boot loader (SBL) that puts the device in Boot ROM mode and opens the COM port. Some forensic tools use it to extract user data.
I used Passware Kit Mobile to perform an extraction of Huawei P40e lite (ART-L29) kirin 710 chipset, android 10, security patch 01/12/2021, locked 6 digits.
I launch PKM and select the device.
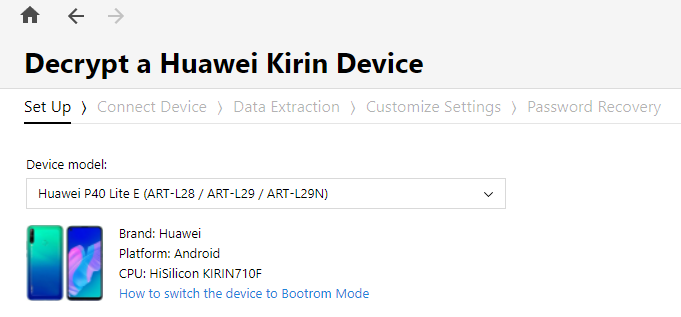
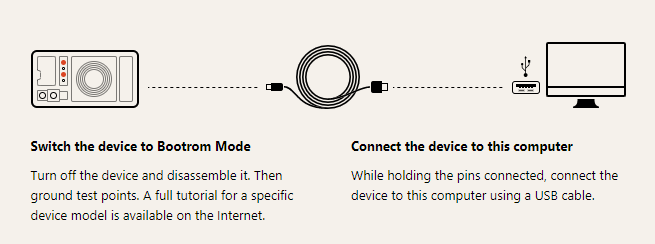
- First, I needed a Harmony TP cable that allows the device to enter USB COM 1.0 mode.
- Disassemble the device to access to test points.
- Disconnect the battery
- Tweezers for shorting test points.
Short the test points and connect the device to your computer by USB.

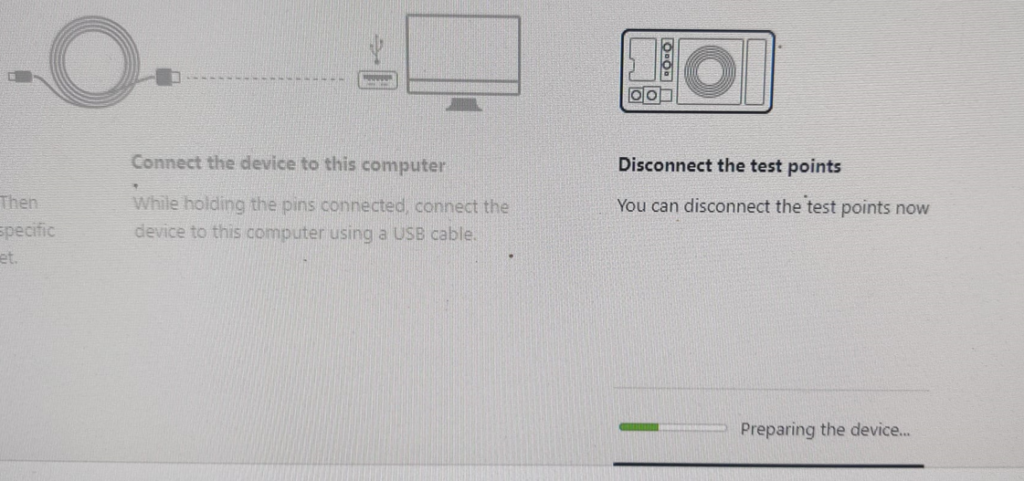
During « Preparing the device » reconnect the battery.
After extracting the encrypted user partition (50.8GB in 28 minutes), brute force process started.
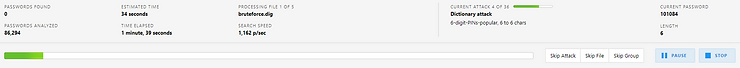
The code was found very quickly and PKM decrypted the dump (17.7 GB in 6 minutes).