Since iOS 9.3 you can secure notes that have your personal data, like financial details, medical information, or website logins — with a password, Face ID, or Touch ID.
For decryption you will need of hashcat, Strawsberry, script pearl to get locked note’s hash and a dictionnary.
First, install Strawsberry and launch perl script to get hashes.
C:\Strawberry>iOS_notes.pl NoteStore.sqlite > hash.txt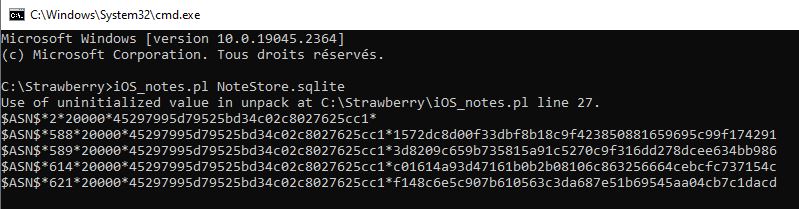
I created two dictionnary based on the data from the extraction with Physical Analyzer from Cellebrite .and Wordlist Generator from Magnet Forensics.
hashcat.exe -m 16200 -a 0 hash.txt Dictionnary.txt- -m : hash type
- 16200 : Apple Note secure
- -a 0 : Attack mode straight (trying all words in a list)
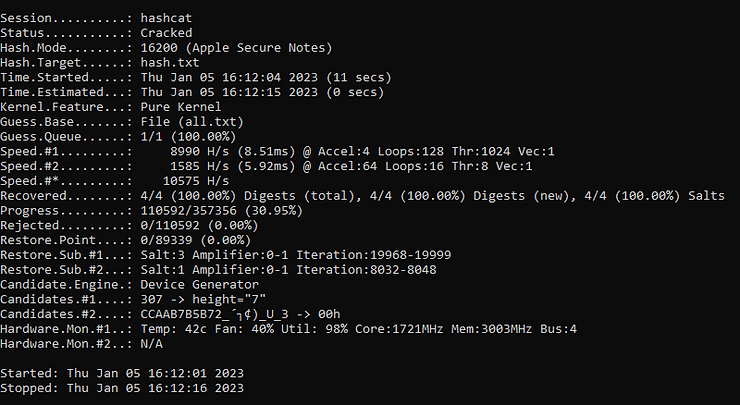
« Cracked » indicate that the result is in hashcat.potfile. If you make tests don’t forget to delete it. if all the hashes were tested unsuccessfully, the status would be « exhausted ».
PA decrypted notes with theses dictionaries but it took time compared to hashcat.
SQLite query to find encrypted Notes (works on iOS15) :
SELECT ZICCLOUDSYNCINGOBJECT.Z_PK,
ZICCLOUDSYNCINGOBJECT.ZCRYPTOINITIALIZATIONVECTOR,
ZICCLOUDSYNCINGOBJECT.ZCRYPTOTAG,
ZICNOTEDATA.ZDATA
FROM ZICCLOUDSYNCINGOBJECT, ZICNOTEDATA
WHERE ZICCLOUDSYNCINGOBJECT.ZISPASSWORDPROTECTED=1 AND
ZICNOTEDATA.ZNOTE=ZICCLOUDSYNCINGOBJECT.ZCLOUDSTATE
